5 Network Security Vulnerabilities and How to Avoid Them
As data breaches continue to grow in severity and frequency, it’s evident that organizations need to improve their vulnerability management to safeguard their sensitive information better.
Considering that data breaches are up 4.3% from 2021 and average $9.44 million, now is the time to take the appropriate action.
Given the rising risks that cyber threats and vulnerabilities continue to play in business today, we’ve drafted this blog to address the following:
- Network security vulnerabilities
- Types of network security threats
- How to manage and overcome these identified cyber vulnerabilities and threats
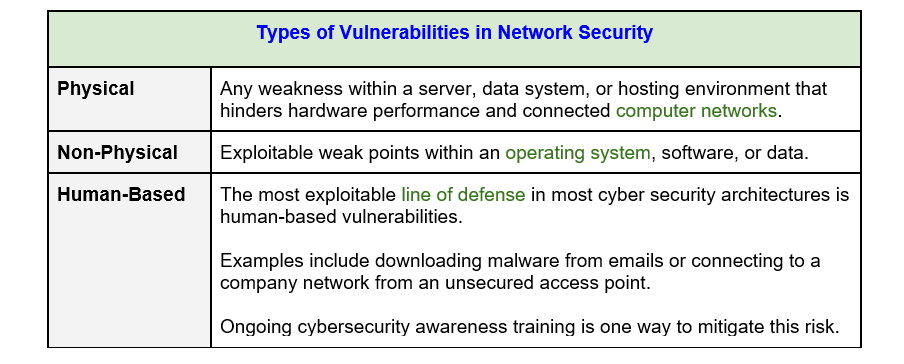
Types of Vulnerabilities in Network Security
Network vulnerabilities are underlying weaknesses that reside within an infrastructure. As with most vulnerabilities, network security vulnerabilities are exploitable, often providing cybercriminals with unauthorized access to private company messages, files, and network devices.
In general, network vulnerabilities generally fall into one of three categories, which include:
When you consider how the average cost of unplanned downtime is $22,000 per minute in some industries, protecting your sensitive data and business from a security breach is critical. Let’s explore the five most common network security vulnerabilities and how to mitigate them.
Protect Your Business With Two-Factor/Multi-Factor Authentication
Learn about the difference between 2FA and MFA and their importance.
5 Common Network Vulnerabilities and How to Overcome Them
1. Misconfigured Firewalls
When cybercriminals gain access to your infrastructure, they not only have the ability to steal data but also can inject malicious code that siphons your productivity, spies on internal communications, or creates additional vulnerabilities that a bigger cyber attack can later exploit.
To bolster your firewall defenses, relying on managed security services is a great way that businesses can strengthen their data protection with ongoing managed firewall support.
2. IoT Devices
Internet of Things (IoT) devices possess significant cyber security vulnerabilities.
In addition to having access to sensitive identifying information about you, most Smart devices lack sufficient cybersecurity protection, which creates hidden vulnerabilities within organizations. For example, many businesses use Smart thermostats, Bluetooth speakers, and surveillance cameras that lack sufficient data protection and are susceptible to network security attacks.
Why? Because the majority of those devices aren’t created with adequate security.
A couple of ways that businesses remove IoT vulnerabilities is by creating and deploying security and access controls or by outsourcing their security responsibilities to a trustworthy IT company.
3. Physical Device Security
Physical access continues to be a major vulnerability in network security. While many organizations are smart enough to avoid using unsolicited devices (such as fakely gifted USB drives infected with malware), any device that accesses a company network, such as a mobile device, tablet, smartwatch, and laptop, requires monitoring, securement, and full-time support.
To remediate physical device vulnerabilities, many businesses implement a web filtering gateway, conduct routine vulnerability scans, perform remediations, and ensure endpoints are always protected.
4. Poor Email and Password Protection
Business email compromise is the leading cause of data breaches. Considered a human-based vulnerability, many employees fail to make a strong password (or, more commonly, use unique passwords for their credentials) which creates enormous security risks.
Among the most common approaches for remediating these vulnerabilities include:
- Using two-factor authentication
- Using only strong, unique passwords
- Deploying anti-spam/malware/virus email filters
- Never accessing a company network from a public Wi-Fi connection
- Monitor employee emails, their habits, and use ethical hacker services
5. Social Engineering Attacks
One of the most dangerous types of attacks in network security threats include social engineering attacks, like phishing, smishing, whaling, and tailgating, are the second leading cause of data breaches and accounted for 16% of data breaches in 2021.
Proving easier to bypass than authentication and authorization protocols, it’s predicted that social engineering attacks will continue to grow in impact and frequency as businesses continue to embrace remote work and bring-your-own-device (BYOD) policies.
Some ways that businesses overcome social engineering attacks would be by:
- Gaining 24/7 network performance monitoring
- Performing routine penetration and remediation services
- Strengthening your infrastructure through cloud-powered solutions
- Outsourcing your IT security to a trusted managed service provider
Interested in learning more about network vulnerabilities? Check our these blogs:
- Ransomware Removal Recovery
- Stay Protected From Ransomware
- Bell Canada Hack Reminds Business Leaders to Take IT Security Seriously
Avoid Information Security Vulnerabilities With Cloud9 Solutions
When network vulnerabilities are allowed to go unresolved, they increase security risk for:
- Data loss
- Downtime
- Compliance fines
- Irreparable reputational damages
As an organization, you have more important matters to focus on which is why Cloud9 Solutions is here to assist you.
Our security experts specialize in identifying, remediating, and preventing future network security vulnerabilities. Additionally, our services are trusted by more than 100 businesses and will elevate your organization’s security posture and data protection while eliminating cyber vulnerabilities from your infrastructure.
With us in your corner, support is never far away. For more information about our network services, contact us today.
