When was the last time you got spam email? Even with a good anti-spam filter in place, junk emails still can come through. Imagine that one day, as you scan your inbox, one message seems to stand out. It appears as though this mail is from your current bank; “Your account has been compromised, please download our form to confirm your identity”. You download the form and upon reading through it quickly realize it is a scam. Whew, good thing you didn’t send it in – disaster avoided right? Wrong. You’ve been infected with ransomware. So what is ransomware and what did you do wrong? This article will explain how ransomware affects you and how to stay protected.
What is Ransomware?
Ransomware is a complex piece of malware that can block the victim from accessing their files. The only way to regain access is to pay a ransom fee. Unfortunately, simply paying the fee does not guarantee that your files will be unlocked. In the case they actually are unlocked, there’s no saying when they will encrypt them again.
There are two main types of ransomware:
Encrypting ransomware
This type of ransomware is designed to let your system continue running, but completely block access to any system files. It uses encryption algorithms that can only be decrypted when the victim pays for the decryption key.
Locker ransomware
This type will just lock the victim out of their system altogether. The victim’s files are not encrypted, but all access to them is cut off. In this case, the victim will have to pay the attacker to unlock their computer.
Origins and Operations of Ransomware
Believe it or not, the first ransomware attack was back in 1989. Known as the “AIDS Trojan”, it spread via the floppy disk which, once inserted into a computer, would hide it’s payload on the hard drive and would only encrypt file names, along with a popup that blamed the encryption on an expired license key. To get the decryption key, you would then have to send a ransom of roughly $190 to a PO box in Panama.
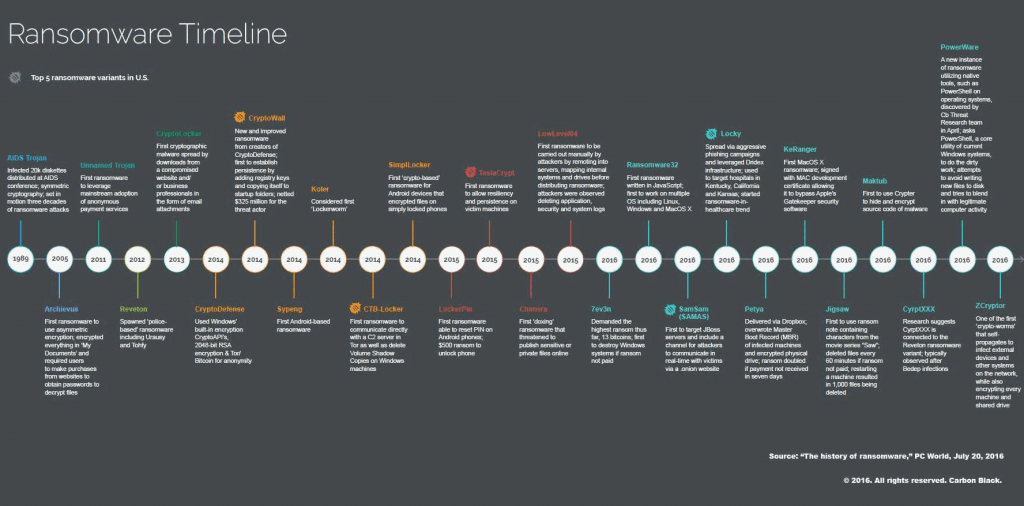
Obviously the times have changed a lot since the days of the floppy disk but unfortunately, the cyber threats are keeping pace with our advancing world of technology. With the creation of bitcoin and the evolution of encryption algorithms, ransomware has matured from a minor act of cyber vandalism to a mature money-making illegal global business. In 2017, 6 in 10 malware payloads were ransomware. You can tell from these numbers that the creators of ransomware are completely remorseless.
How Do Ransomware Threats Spread?
At its core, these cybercriminals are looking for the easiest way they can reach as many people as possible and then infect their systems. The number of styles that these criminals use to spread ransomware is continually changing and growing. However, there are some styles that are more effective than others.
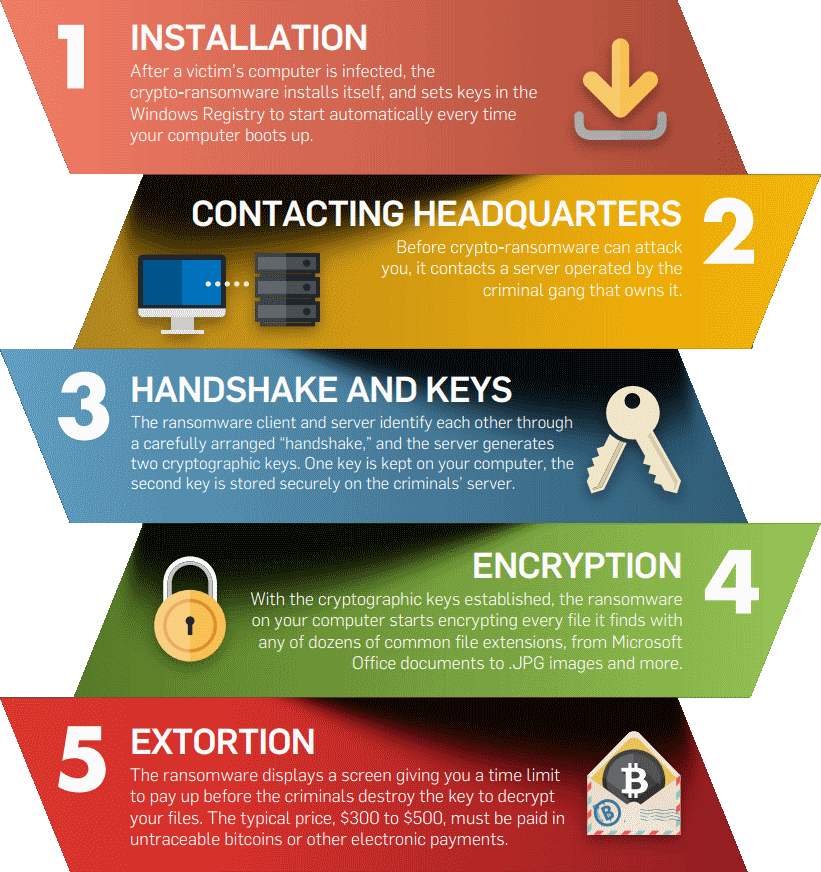
You have most likely already come into contact with some of these attacks as one of the most common methods used is spam email campaigns. These emails are automated and are sent out to anyone and everyone. These emails will contain a malicious link or file attachment, that when clicked will deliver a security exploit to create a backdoor inside the victims PC.
Another popular method used is self-propagation, where each infected computer will spread it to another. The most famous version of this style is the WannaCry attack. WannaCry used an exploit kit that scanned a user’s PC looking for a certain vulnerability, then it launched a ransomware attack that targeted it. As of May 24, 2017, this infection has affected over 200,000 victims in 150 countries and it continues to spread.
How Can I Protect Myself?
Most cybercriminals know how easy it is to lure users into clicking the links sent out in an email. From subject lines like “Confirm your purchase” or “Unpaid invoice” or “Suspicious activity on your account, please confirm your info” are all designed to trick you into engaging with them.

The best thing you can do in the case of a suspicious email is to analyze every section of it. From the text in the subject line to each word in a file attachment or link, you can never be too cautious. Aside from emails, there are many precautions you can take to protect yourself in the event you do get a cyber infection.
Precautions
- Regularly backup your files and computer to an external drive. It’s important that you do not leave the external drive connected to your computer. Many ransomware programs will encrypt files on it as well.
- Stay away from suspicious websites that could contain malware downloads or offer seemingly free programs that contain hidden malware content.
- Don’t cheap out in your anti-virus protection. Use a proper protection program and keep it up to date.
- Don’t skip your operating system’s updates. Many of these system updates include new protection methods to resist a cyber attack
If an entire business operation runs from their own local PCs or servers, the stakes are high. Should they do get hit by ransomware, their entire system can come crashing down. With operations like hospitals and other large corporations getting hit by ransomware attacks, is there any hope that an SMB can stay protected or withstand an attack?
The Cloud9 Solution
If you are having difficulty determining which type of security protection is right for you, why not let an experienced professional work with you to ensure that your security is robust, efficient and cos-effective.
Cloud9 offers many variations of security consulting such as all of which are designed to fulfill your security needs and most important; give you peace of mind. If you have had any breaches in the past, the Cloud9 team can investigate and determine what went wrong and how to prevent it from reoccurring.
With our Private Cloud services, you can also rest easy knowing that all of our services are leading-edge technologies found in modern private cloud networks of today.
Contact Cloud9 today to request a quote for a solution that is designed to perfectly fit your infrastructure.

